Symmetric vs Asymmetric Encryption

Picking an encryption program to safeguard confidential information might be difficult for someone who isn't a techie or isn't familiar with cryptography.
So, Symmetric vs Asymmetric encryption, what's the difference?
Let's find out!
Skip to
Encryption Explained
The process of turning a readable set of data (plaintext) into an incomprehensible cypher is known as encryption.
The information is scrambled as an outcome of an algorithmic procedure involving a unique cryptographic key.
To put it simply, encryption captures your information and randomizes it enough that anyone who obtains it won't understand it unless they have the special unique key to decrypt the data.
We must employ encryption if we desire confidentiality and safeguard our data at rest, in use, or in transit.
This post will examine and compare the two basic forms of encryption: symmetric and asymmetric encryption.
What is Symmetrical Encryption?
When symmetric encryption is applied, the very same key is used to both encrypt and decode communications.
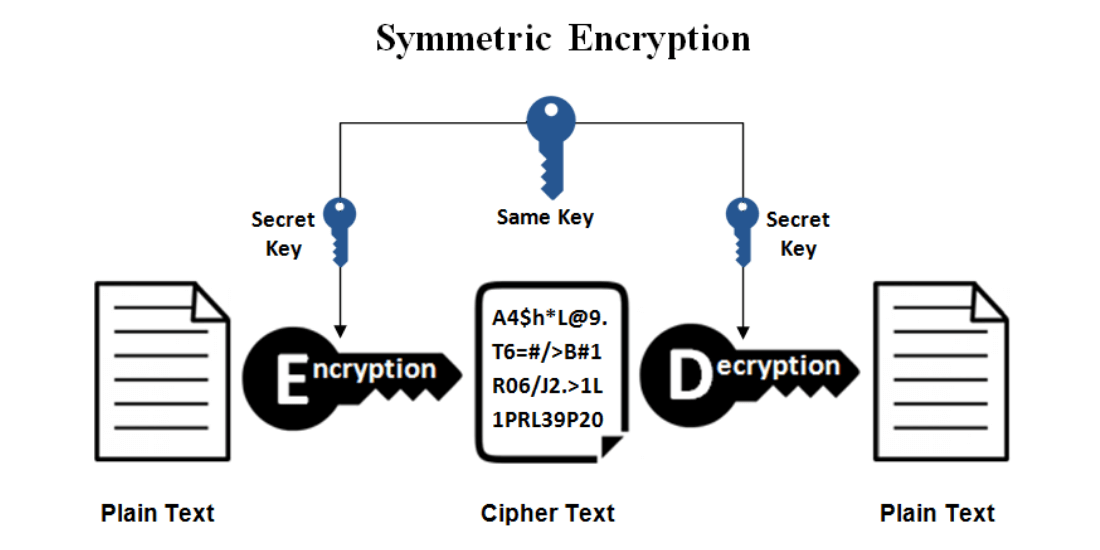
The overall process does not expand effectively because the key must be kept a shared secret — that is, it must be exchanged with the receiver safely so that only they can use it to decode the message.
Block or stream cyphers can be used in symmetric encryption techniques.
A block cypher encrypts a group of bits (in chunks) as a single entity.
AES, for example, employs a block size of 128 bits with three distinct key length choices: 128, 192, or 256 bits.
Symmetric encryption faces key depletion concerns. Without adequate maintenance of a key history or effective key renewal, every usage might likely reveal information that can be possibly exploited by an assailant to reassemble the secret key.
Although symmetric encryption has access control difficulties, it is quicker and operates without overhead costs on networking or CPU assets.
Therefore, it’s commonly used in tandem with asymmetric encryption, which we’ll cover next and compare to symmetric encryption.
Benefits of Symmetric Encryption
Symmetric encryption is utilized nowadays since it can rapidly encode huge quantities of data, and it's simple to execute.
It’s easy to use, and its AES version is among the safest data encryption methods accessible.
Furthermore, symmetric encryption has numerous advantages over its asymmetric cousin, but we’ll briefly discuss asymmetric encryption in this blog article.
- Protection: symmetric encryption methods like AES need billions of years to crack, even with ruthless assaults.
- Speed: symmetric encryption is significantly faster due to its smaller block size and easy operation than asymmetric encryption.
- Industry acceptability and approval: symmetric encryption techniques like AES have established the global standard of data encryption due to their security and speed merits.
As such, they have experienced generations of industry adoption and integration.
Downsides of Symmetric Encryption
Arguably one of the few drawbacks of symmetric encryption is using a singular, secret encryption cypher key to encrypt and decode information.
So why is that?
Well, if these cryptographic keys are placed in an unsecured position on a system, then cybercriminals may obtain access to it via software-based assaults, enabling them to decode the encrypted information and therefore undermining the primary function of symmetric encryption.
In fact, if one party or institution is encrypting at one place and a different party or entity decoding at a different one, then the keys will need to be transferred, making it subject to detection if the transmission media is breached.
That’s why it’s important to maintain the safety of the encryption algorithm or key whether you're at rest or in transit.
Alternatively, you’re basically asking for a plethora of autonomous and state-sponsored cybercriminals to steal your operation-critical, safety-critical, or legally recognized confidential data.
Perhaps the only downside of adopting symmetric encryption is its protection effectiveness when matched to asymmetric encryption, which is usually believed to be safer but is also slower to perform than symmetric encryption.
However, is asymmetric encryption better and more reliable than symmetric encryption?
Let's take a look...
Key Features of Symmetric Encryption
There's only one shared encryption key that is used around for decoding and encrypting at a time.
It doesn’t grow very well since the secret key should not be stolen or distributed to unauthorized users, or else they might decode the text.
What is Asymmetric Encryption?
Asymmetric encryption utilizes a combination of two linked keys – a public and a secret key.
The public key, which is available to all, should encode plain text before actually transmitting it.
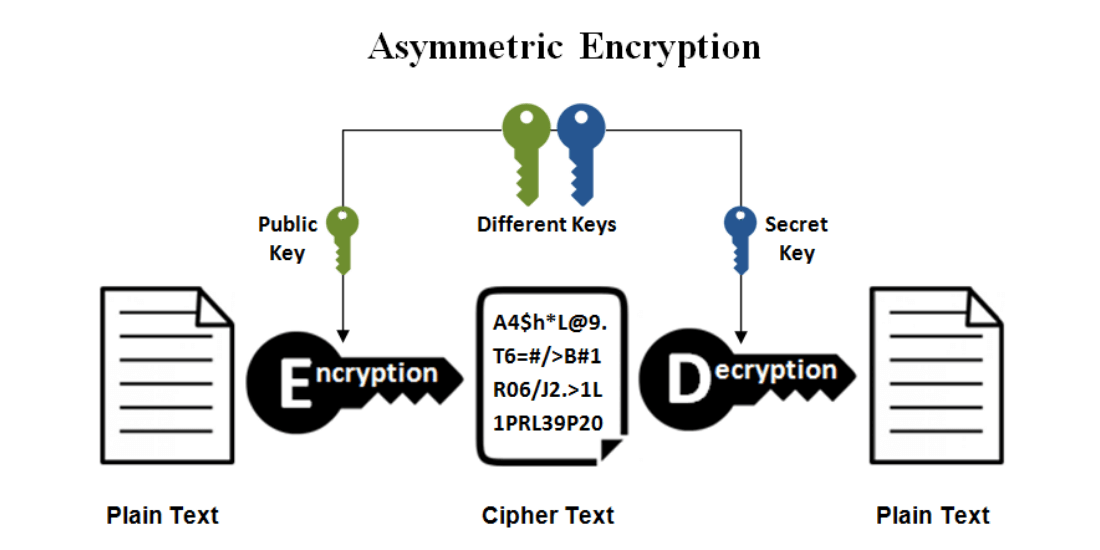
To decode and see the message, you have to possess the secret key. The public and the secret keys are technically linked, but the secret key cannot be deduced from that.
In asymmetric encryption (also known as public-key encryption or public-key cryptography), the secret key is only communicated with the key’s originator because its protection has to last for a long time.
Since asymmetric encryption has a more complex operation than its symmetric equivalent, the time needed is higher.
However, this kind of encryption provides a greater degree of safety as opposed to symmetric encryption because the private key is not intended to be disclosed and is kept hidden.
This is also a much more flexible approach.
Asymmetric Encryption in Digital Certificates
To utilize asymmetric encryption, there must be a method of finding public keys.
One used method is utilizing digital verifications in a client-server setup of communication.
A certificate is a bundle of data that verifies and identifies a user and the concerned server.
It includes data such as the name of organizations, the entity that passed the certificate, the users’ email address and location country, and even the users' public key.
When a server and a user need a securely encrypted connection, they send a request across the internet to the other side, which actually sends a certified copy.
The other entity's public key may be retrieved from the certification. A certificate may also be used to authenticate the owner.
SSL/TLS utilizes asymmetric and symmetric encryption, and you can rapidly glance at digitally authenticated SSL certificates issued by trustworthy certificate authorities (CAs).
Benefits of Asymmetric Encryption
Key distribution is not essential: protecting key distribution routes has long been a problem in cryptographic encryption. Asymmetric encryption eradicates data encryption.
The required public keys are transferred via public-key servers, and the revelation of public keys is not, at this moment, harmful to the safety of encrypted communications since they cannot be used to deduce secret keys.
Transfer of secret keys not required: with asymmetric encryption, private keys must be kept safely and therefore secret to the organizations utilizing them.
Essentially, the keys required to decode sensitive data aren't ever, and should never be, transferred via an easily hackable communication channel, and that’s a big positive for the security and reliability of strong encryption.
Digital signature/message verification: using asymmetric encryption, senders may use their secret key to digitally approve and authenticate that a message or document came from themselves and not an unknown foreign entity.
This may seem like there really no going bad with asymmetric encryption. After all, why would you really select symmetric encryption if asymmetric cryptography is so safe?
One phrase... "better speed!"
Downsides of Asymmetric Encryption
The primary drawback of asymmetric encryption is that it’s more time-consuming and slower than symmetric cryptography because of its larger key sizes, not to forget that asymmetric encryption computations appear to be considerably more complicated than their symmetric equivalents.
So, why is that?
Basically, in principle, public keys could be used to break secret keys – remember, they’re mathematically connected – but asymmetric encryption employs substantial key sizes to make this nearly impossible, at least as of now.
So, in essence, symmetric encryption is quicker than asymmetric encryption.
Asymmetric encryption trades speed for safety, whereas symmetric encryption compromises protection for speed.
Now, this does not mean that symmetric encryption is unsafe; nevertheless, the basic basis of asymmetric encryption removes many information security issues that remain inside badly managed symmetric cryptographic systems.
Key Features of Asymmetric Encryption
It includes the use of 2 mathematically connected keys.
The public key (the one everyone knows) and the private key (that is only available to you) are needed to encrypt the communication.
The secret key cannot be retrieved from the public key.
The public key is used by everyone else to encode the communications they transmit to you, but to decode and read this information, one requires access to the secret personal keys.
Symmetric vs Asymmetric Encryption
As we’ll describe soon, there are five major distinctions between symmetric and asymmetric cryptography.
Some of these variations pertain to the kinds of keys utilized but others connect to how much time the encryption techniques require to calculate.
So, when we speak about symmetric versus asymmetric cryptography, which is safer?
Asymmetric encryption is a more protected one clearly, whereas symmetric encryption is quicker.
They’re both extremely successful in various methods and, based on the job at hand, one or the other may be employed either alone or together with one another.
Maybe, you now have a grasp of the basic key difference between symmetric encryption versus asymmetric cryptography.
The table below offers a more in-depth contrast between symmetric versus asymmetric cryptography:
- Symmetric Key vs Asymmetric Key
Symmetric – Only one key (symmetric key) is used, and the same key is used to encrypt and decrypt the message.
Asymmetric – Two different cryptographic keys (asymmetric keys), called the public and the private keys, are used for encryption and decryption.
- Complexity and Speed of Execution
Symmetric – It’s a simple technique, and because of this, the encryption process can be carried out quickly.
Asymmetric – It’s a much more complicated process than symmetric key encryption, and the process is slower.
- Length of Keys
Symmetric – The length of the keys used is typically 128 or 256 bits, based on the security requirement.
Asymmetric – The length of the keys is much larger, e.g., the recommended RSA key size is 2048 bits or higher.
- Usage
Symmetric – It’s mostly used when large chunks of data need to be transferred.
Asymmetric – It’s used in smaller transactions, primarily to authenticate and establish a secure communication channel prior to the actual data transfer.
- Security
Symmetric – The secret key is shared. Consequently, the risk of compromise is higher.
Asymmetric – The private key is not shared, and the overall process is more secure as compared to symmetric encryption.
- Encryption file size
When compared to the original plain text file, the encrypted text is smaller.
When compared to the original plain text file, the encrypted text is larger.
- Utilization of Resources
Symmetric - is based on a low resource consumption model.
Asymmetric - requires a lot of resources.
- Examples of Algorithms
Symmetric – Examples include RC4, AES, DES, 3DES, etc.
Asymmetric – Examples include RSA, Diffie-Hellman, ECC, etc.
- Safety
Symmetric – Due to the usage of a sole key for encryption, the system is less safe.
Asymmetric – Encryption and decryption process uses two keys, making them more secure.
- Quantity of Keys
Symmetric – For encrypting and decrypting, symmetric cryptography employs a single key.
Asymmetric – For encrypting and decrypting, asymmetric cryptography includes two keys.
- Time Consumption
Symmetric – It's a time-saving method.
Asymmetric – It's a cutting-edge encryption method.
- Confidentiality
Symmetric – When using a unique key for encrypting and decrypting, there is a risk of the key being stolen.
Asymmetric – Two keys, one for encryption and the other for decryption, eliminate the need to exchange a key.
SSL/TSL Handshake
When we browse the web using the unsecured HTTP protocol, data flows in an unprotected manner that anybody sitting in on the connection may readily capture and steal.
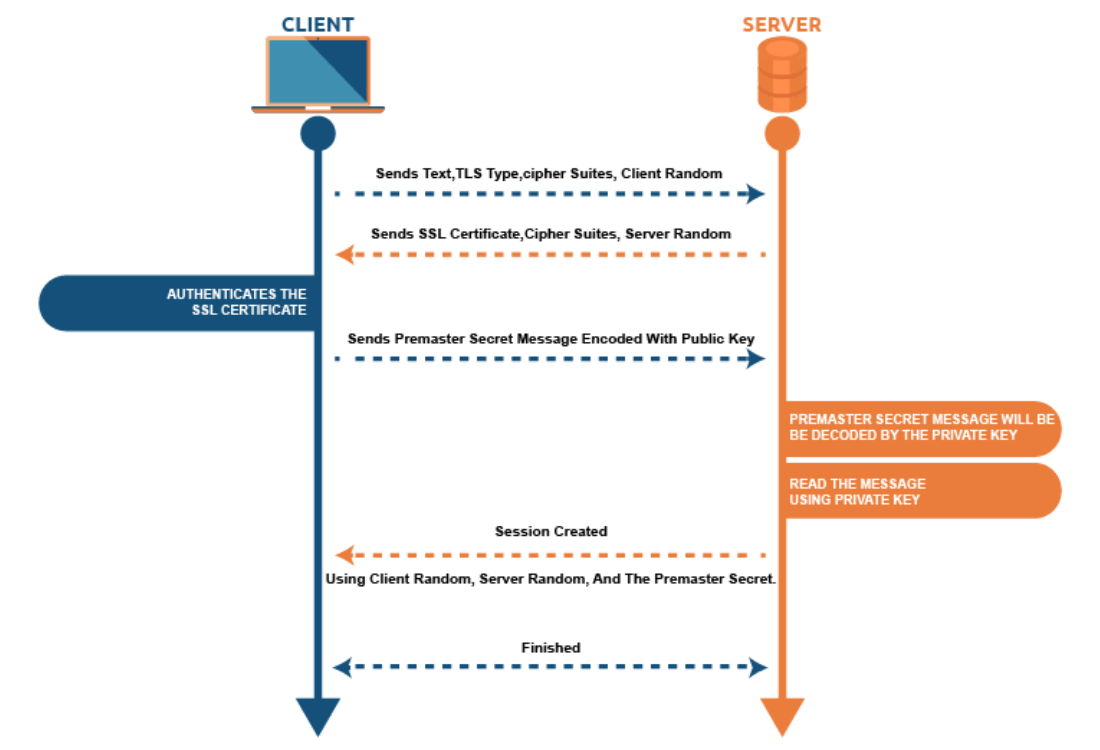
SSL/TLS certifications secure the channel of communication between both the user (web browsers like Opera, Safari, and others) and the servers you're trying to connect to, allowing you to surf safely via HTTPS.
While the handshake has many stages, the encryption procedure (which starts with asymmetric cryptography and then transitions to symmetric encryption for bigger transmissions) only takes a few moments.
When we use HTTPS to access a website, a secure communication channel is created between our user's computer and the website's host.
Let's take a quick look at how encryption is used while establishing up a reliable link:
Settlement of a Connection
The SSL/TLS procedure starts with the client welcome signal, which, among other things, conveys the available cipher suites after the 3-stage handshake between the sender and receiver (e.g., RSA, Diffie-Hellman, etc.).
The link is made using the strongest encryption level that both the browser and the server support.
Sharing of Secret Keys
The client gets the server's digital certificate, which contains its public key, with the server welcome message.
After validating the authenticity of the server certificate, it utilizes this key to create a pre-master password.
After encrypting the pre-master password with the public key, the client transmits it to the server.
The server decrypts and obtains the same pre-master code using the secret keys.
Depending on the content of the pre-master secret key, both the sender and receiver compute the symmetric key independently.
Specify a new cipher
Both the sender and the recipient send a modified cipher spec signal after computing the symmetric key.
This means any future interaction requiring mass data transmission will be conducted via a safely encrypted channel utilizing symmetric keys (encryption protocols such as AES).
Wrapping Up
We've covered almost all there is to know about symmetric vs. asymmetric encryption.
Questions like "what's the difference between symmetric and asymmetric cryptography" and "symmetric key versus asymmetric key" should be answered by now.
Despite the fact that they are vastly different due to distinct mathematical structures, they have both found use in a variety of situations.
Symmetric encryption, for example, is used to secure file content or appears in hardware encryption, whereas asymmetric encryption is applied with an electronic signature.
A mixture of both of these methods, in addition to SSL, is utilized in a variety of different situations.
End-to-end cryptography is utilized by messaging apps like Signal and WhatsApp, where asymmetric encryption has been used to establish the secured communication channel and symmetric cryptography is used for the remainder of the discussion.
When it comes to cryptography, the most recent methods aren't always the safest.
Always choose the cryptographic algorithms which are the most appropriate for the job at hand.
In reality, as cryptography evolves, new algorithms are being created in order to keep up with intruders and safeguard data in order to improve secrecy.
In the future years, hackers will undoubtedly make life difficult for professionals, so anticipate more from the cryptography community!
